Top Password Attacks: How to Protect Against Brute Force, Dictionary & Keylogger Threats
Several kinds of cyberattacks are prevailing around the globe but some manage to dominate and cause utter damage to both the privacy and security of information. This seems to increase in number and change its consequence with each passing day. Even stringent prevention techniques are not being sufficient to discourage hackers to check themselves.
This article tries to draw your attention to one of the most common types of attack that a user becomes victim to and that is a Password Attack.
What is a Password attack?
This refers to any of the different methods used by Cyber criminals to maliciously creep into password-protected accounts. These attacks are typically executed through the use of software that expedites cracking or guessing the passwords.
Among the various techniques, the three most common methods used to break into a password protected system are:
Brute-force attack
This kind of attack is basically a trial-and-error method that takes place when a hacker uses a computer program or script to try logging in with possible password combinations by systematically cycling through each letter in a character set. A character set could be letters, symbols, numbers etc.

Dictionary attack
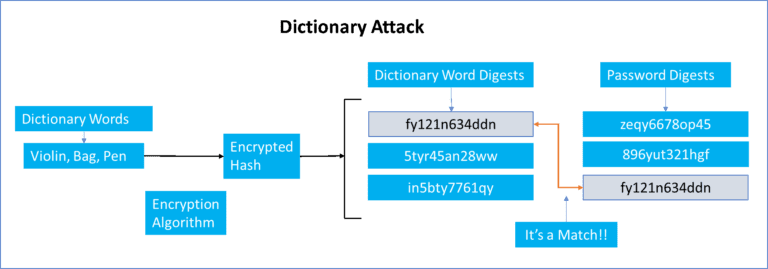
As soon as a user creates a password it is taken and hashed using a key known to the site. The hash value (a short string of letters and/or numbers) is then derived from the combination of both the password and the key, using an encryption algorithm. When hackers get access to passwords, they actually get access to the encrypted hash.
In this dictionary attack, a hacker uses a program which tries to log in to systems by cycling through the combination of common words found in the dictionary. He uses a word list where every word is hashed and when the cracking software matches the hash output from the dictionary word to the password hash, the attacker successfully identifies the original password to extract sensitive information.
Keylogger attack
Keyloggers are malicious software installed in the targeted system from an unknown source, without the user’s knowledge and designed to track the activities of a particular user. A hacker uses this spyware to trace and record all the keystrokes of an individual so that critical information like login IDs and passwords for all the applications could be recorded and reported back to him. All keyloggers first follow the keystrokes and then store them in a file or forward them to the hacker over the internet using mails or through FTP servers. Internet history could also be recorded through this attack. To prevent this kind of hacking, multi factor authentication method has been introduced as a must have for all businesses and organizations.

Ways to prevent Password Attacks:
1. It’s important to ensure that passwords are as complex as possible. Use strong passwords, unique passwords (for every account) and change them every 3 months. Ideally, passwords should have more than 12 characters, and be composed of random numbers, symbols, and letters.
2. An automated pen testing tool can be used to quickly run password attacks.
3. Use MFA to put additional roadblocks in the way of attackers in order to log in. The more requirements there are, the more time it will take for an attacker to gain entry. MFA adds more barriers and each barrier needs to be very robust.
4. Monitoring activity with a SIEM can flag an unusual amount of login attempts, automatically escalating the issue to the security team, allowing them to quickly prevent or neutralize risks.
5. Password focused tools like password managers and MFA must be paired with other solutions, like antivirus and other forms of threat detection.
6. Personal information like names, birthdays, addresses, or phone numbers should not be used as passwords.
7. Using public Wi-Fi without a VPN allows hackers to track your online presence and potentially expose your device’s data
Statistics:
Individuals and stolen password consequences:
4 out of 10 people had their data compromised online. (Google, 2019)
80 percent of data breaches that involved hacking are connected to passwords. (Verizon, 2020)
63 percent of consumers fear their identity would be stolen. (Norton, 2021)
Businesses and stolen password consequences:
Across all sectors, it took 280 days on average to identify and contain a data breach. (IBM, 2020)
59 percent of U.S consumers are likely to avoid businesses with organizations, that have become a victim of a cyberattack in the past year. (Arcserve, 2020)
68 percent of business leaders feel that the risk of experiencing a cyberattack is increasing. (Accenture, 2019)
